There is a general misconception about security today. Most people would love to believe that their firewalls are completely capable to protect them from anything indecent. The sad part, they could not be more wrong. Hungry Hacker aim to prove it with three separate programs that can compromise the security of computers. You have the opportunity to say “What’s a backdoor?” Yes, these programs were created in 1990, but still pose a real threat today. It is the first two that are still being developed.
Using these programs any noob can remotely access your computer without any Authentication and do whatever he wants. I will tell you some of the features rest of them you need to try it and find out. These Programs :
- Work as a key logger.
- Send any Information from Victim’s PC to the Hacker’s PC.
- Run any program on the Victims PC.
- Display any Violating Image on victim’s Screen.
- Open the CD Drive of the Victim’s PC.
- Open any Web page on the Victims Screen.
- Disable any Specific Key or whole Keyboard.
- Shutdown Victim’s PC.
- Start a Song on the Victim’s PC.etc.etc…………..
Back Orifice / Back Orifice 2000
Back Orifice is one of the most common backdoor programs, and one of the most deadly. The name may seem like a joke, but sure, the threat is real. Back Orifice was established in Cult of the Dead Cow group. Back Orifice is an Open Source Program. The main Threat of this software is that by making some changes in the code anybody can make it undetectable to the Anti virus Program running on the Victim’s computer. Apart from the strange title, the program usually gets port 31337, the reference to “Lit” phenomenon is popular among hackers.
Back Orifice uses a client-server model, while the server and client is the victim attacker. What makes Back Orifice so dangerous that it can install and operate silently. There is not required interaction with the user in, meaning you could its on your computer right now, and do not know.
Companies such as Symantec have taken steps to protect computers against programs that they consider dangerous. But even more attacks using Back Orifice 2000. This is due partly to the fact that it is still evolving, as open source. As stated in the documentation the goal is ultimately the presence of the Back Orifice 2000 unknown even to those who installed it.
Back Orifice 2000, developed for Windows 95, Windows 98, Windows NT, Windows 2000 and Windows XP.
Where can I download Back orifice 2000?
Back Orifice 2000 can be downloaded at the following address: http://sourceforge.net/projects/bo2k/
I infected! How do I remove it?
Removing Back Orifice 2000 may require that you change the registry settings. To remove it at 7 simple steps, refer to the diagram below.
How do I delete Back orifice 2000
- Click Start> Run, and type “Regedit”(without the quotes)
- Follow the path below: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices “
- Now looking in the right box: “The umgr32 = ‘c: \ windows \ system \ umgr32.exe”
- Right-click on this entry and click Remove. Now restart your computer.
- After restarting only open Windows Explorer. Make sure you can see all registered extensions. To do so, select “View Options and configure the appropriate settings.
- Go to the WINDOWS \ SYSTEM directory, and find “umgr32.exe” file. Once you find it, delete it.
- Exit Windows Explorer and reboot again.
NetBus / Netbus 2.0 Pro
NetBus was established around the same time that the Back Orifice was in the late 1990’s. NetBus was originally designed as a program prank friends and family, of course anything too malicious. However, the program was released in 1998, and is widely used as a backdoor to manage computer.
Like the Back Orifice, NetBus allows attackers to do virtually everything in the computer victim. It also works well under Windows 9x systems, as well as Windows XP. Unlike Back Orifice, the latest version of NetBus regarded shareware is not free. NetBus is also implementing less stealthy operations, as a direct result of criticism and complaints of abusive use.
Where can I buy and download NetBus?
NetBus can be purchased and downloaded at the following address: http://www.netbus.org/
Ok, I am infected. Now what?
Fortunately, the latest version of NetBus is a valid program. It can be removed just like any other program. Previous issuance NetBus is a bit more tricky, however. If you are not lucky enough attacked with the latest version, the withdrawal process and in the Back Orifice.
How do I remove NetBus?
- Click Start> Run, and type “Regedit ‘(without the quotes)
- Follow the path below: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices “
- Now, in the right box, looking as follows: “[Name_of_Server].”Exe Of course, you have to find the actual name of this file EXE-. Usually This” Patch.exe ‘or’ SysEdit.exe “, but may vary.
- Reboot and remove all traces of the actual program, which can be left. Additionally, you can set yourself NetBus, and then use its own function disposal.
SubSeven / Sub7
SubSeven or Sub7, has been established for the same purpose was to NetBus pranks. Sub7 actually has more support for pranks, and has more advanced users. Sub7 also widely used by the script kiddies, although that many firewalls and anti-virus software before initialization.
Since Sub7 not supported for several years, the threat is usually very low. Most security programs will not have any problem in ending Sub7 before it has a chance to be started. This shows that the importance to the modernization and security programs is critical, because the money was still there.
Nevertheless, it is widely used by those who have physical access to your firewall, or security programs. If access rights, the tool will work without restrictions.
Where can I buy and download Sub7?
Sub7 not supported more, and hence is not available for download on any legitimate websites. If you were to make a Google search, you would find links to download Sub7. However, this is not the official site, and should be considered dubious and dangerous.
Sounds harmless, How do I remove it?
- End of the following processes through the curator: “editserver.exe, subseven.exe”
- Delete the following files: “editserver.exe, subseven.exe, tutorial.txt.”
Why these programs is absolutely legitimate?
All the basis behind these programs is that they are designed to help people, not harm. While some like NetBus really were originally created for pranks, they switched routes to avoid legal problems.
These programs claim to be the legitimate remote desktop program, although they certainly easily used for malicious use. These programs really should be used to aid or customer support departments. Why all adolescents is to copy these programs goes beyond us, but leave the content of their networks, while computer is a good idea.
The advent of new technology has made these programs in some respects less effective. However, programs such as Back Orifice 2000, yet still evolving, so do not be surprised to learn that he works in the background, waiting for instructions. Since the best defense is a good offense, be sure to save a sharp eye on what is installed on the network computers. After all, an ounce of prevention is worth a pound of cure.
 8 in 1 Keylogger with Cracks
8 in 1 Keylogger with Cracks
 Joining Google Sky and Stellarium is Microsoft’s entrant to the stars, Worldwide Telescope. I’ve been playing around with it for about an hour and it’s pretty cool. It effectively turns every computer that downloads it into a mini-planetarium capable of displaying high resolution images of millions of stars, planets and other celestial.
Joining Google Sky and Stellarium is Microsoft’s entrant to the stars, Worldwide Telescope. I’ve been playing around with it for about an hour and it’s pretty cool. It effectively turns every computer that downloads it into a mini-planetarium capable of displaying high resolution images of millions of stars, planets and other celestial.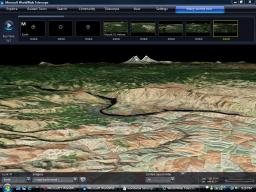 The software allows users to develop their own guided tours of the universe to share with others or take part a guided tour created by astronomy experts.
The software allows users to develop their own guided tours of the universe to share with others or take part a guided tour created by astronomy experts.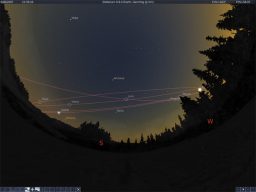 Stellarium is a free open source tool that gives people a chance to access more than 210 million stars, in addition to planets and moons. The project was launched in 2001 and is used in many planetariums.
Stellarium is a free open source tool that gives people a chance to access more than 210 million stars, in addition to planets and moons. The project was launched in 2001 and is used in many planetariums. "
"



