Internet has become a bandwagon of entertainment, education and business. It beats tradition mediums in terms of the benefits it offers. But unfortunately there is much scope of anonymity/privacy on the web and helps the cyber terrorists prey up on the internet resources. That’s why, it is encouraged to learn computer hacking to counter the actions of unethical hackers (also known as black hats).
Hacking is a fraudulent act that is illegal in some ways and helpful in others. It is to know the programmable systems and how they work in a network. An ethical hacker shows the downfalls in the security system of an organization so they can improve it. Today hacking has become an art and very popular that hackers have formed groups and even have conferences together to share their knowledge. Hacking for whatever the purpose, good or bad, requires knowledge and much programming skills. An intelligent programmer can be a good ethical/unethical hacker. These days "hacker" is being used as a term for expert, intelligent and creative people. Let’s discuss how to learn computer hacking:
10 Tips to Learn Computer Hacking
As told before, professional hackers are generally more intelligent than any average programmer. So becoming a hacker depends a lot on one’s intelligence and efforts. However, the following tips will help you learn computer hacking in a systematically.
- Be curious: Curiosity is the mother of hacking. Look under the hood. Take things apart. Know the details of your system directories, file systems, system files. Look inside your computer.
- Read a lot: Buy lots of books, go through the tutorials. Read the help files on your system. If you are using Linux/Unix read the man files.
- Experiment: Take precautions and experiment whatever you read. Apply to work the idea that just hit your mind. Don't be afraid to change things. Doing this for a long time will give you much idea on the computer hardware and the operating system. Try using command options and switches. Tweak the registry and see what happens. Change settings in .INI files. In Linux/Unix, visit the directories where you normally don’t need to go.
- Make backups: If you start mucking around with system files, registries, password files, and such, you will eventually destroy your system. Have a backup ready. If you can afford it, have a system you use just for experimenting, ready to reload on a moment's notice, and do your serious work (or serious gaming!) on a different computer.
- Think out of box: Hacking is not restricted to computers only. You can try trick on other networks also like mobile, telephone, etc.
- Get some real tools: You can find numerous hacking tools on the net. Though some serious tools are not available for free, you need to have some Hex file editors, Snoopers, Compilers and APIs. In addition you also need Scripting tools, Disk editors/formatters and Disassemblers.
- Learn to program: Serious ethical hackers are always very good programmers. If you want to be a hacker, you're going to learn much programming. You should also be quite familiar with the popular operating systems like Windows, Linux, Unix, OS2 etc. Of course, the choice of language depends on you. In Unix and Unix-like OS (Linux, Free BSD) Perl is very good to start with. Use VB or Java to program in Windows. Which ever platform you use, you need to learn considerable C/C++. You should know more than one language because no one language is right for every task.
- Discuss with peers: In isolation, you can’t learn anything. You need to take classes, join users groups and computer clubs. Talking to people on IRC or other chat programs proves really helpful. Share what you learn. Because to get something you have to give some.
- Do some projects: Pick some projects and work consistently until you've finished them. Real time experience is better than reading. Build from ground zero, learn to create icons, associate it with some files, read how the search engines search, try to manipulate the programs that you use daily.
- Use the Internet: There is no source greater than the Internet. Start with the Web. Learn how to use Boolean searches. Bookmark all those sites which you find worth visiting. Sometimes you will find useful information at the most strangest places.
Detailed Courses of Study to Learn Hacking
- Techniques: Windows Hacking, Registries Editing, Password cracks, Google hacking, Computer Forensics, Firewalls, Network Hacking, Security tools, Hacking tools, Encryption, Email tracking, Router Hacking, Email Forging, Port Scanning , MAC Address Spoofing, Proxies etc.
- Tools: Key loggers, Anti Key Loggers, Firewalls, MAC Address Spoofing, Proxy Bouncing tools, Network Scanners like IPscan, Sniffers, Spyware and Trojan Detectors, Information Gathering Tools, Remote Administration Tools, Computer Forensics Tools, Steganography tools and a lot more.
- Games: Hacking Simulation Games to understand the world of hacking and provides you with the opportunity to practice hacking without the danger of getting caught
10 Commandments of Ethical Hacking
- Don’t a computer to harm other people.
- Don’t interfere with other people's computer work.
- Don’t snoop around in other people's computer files.
- Don’t use a computer to steal.
- Don’t use a computer to bear false witness.
- Don’t copy or use proprietary software for which you have not paid.
- Don’t use other people's computer resources without authorization or compensation.
- Don’t appropriate other people's intellectual output.
- Think about the social consequences of the program you are writing.
- Always use a computer in ways that insure consideration and respect for your fellow humans.


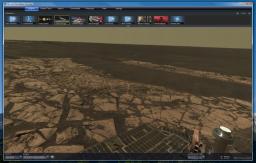 Joining Google Sky and Stellarium is Microsoft’s entrant to the stars, Worldwide Telescope. I’ve been playing around with it for about an hour and it’s pretty cool. It effectively turns every computer that downloads it into a mini-planetarium capable of displaying high resolution images of millions of stars, planets and other celestial.
Joining Google Sky and Stellarium is Microsoft’s entrant to the stars, Worldwide Telescope. I’ve been playing around with it for about an hour and it’s pretty cool. It effectively turns every computer that downloads it into a mini-planetarium capable of displaying high resolution images of millions of stars, planets and other celestial.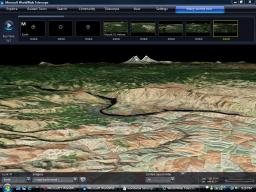 The software allows users to develop their own guided tours of the universe to share with others or take part a guided tour created by astronomy experts.
The software allows users to develop their own guided tours of the universe to share with others or take part a guided tour created by astronomy experts.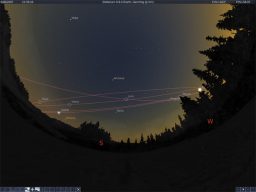 Stellarium is a free open source tool that gives people a chance to access more than 210 million stars, in addition to planets and moons. The project was launched in 2001 and is used in many planetariums.
Stellarium is a free open source tool that gives people a chance to access more than 210 million stars, in addition to planets and moons. The project was launched in 2001 and is used in many planetariums.